Contents
- Vpn Client To Site Cisco Router
- Cisco Vpn Client Windows 10 Download
- Vpn Client To Site Cisco Password
- Vpn Client To Site Cisco Login
- Vpn Client To Site Cisco Remote
- Vpn Client To Site Cisco Server
The VPN Client initiates a connection to a central site device configured to accept these requests. In this example, the central site device is a Cisco IOS Router that uses dynamic crypto maps. When you enable split tunneling for VPN connections, it requires the configuration of an access control list (ACL) on the router. Deezer and sonos. The Cisco VPN Client is a program that allows computers to connect to a virtual private network, which allows users to access the resources for that private network from a remote location as if they were directly connected.
Introduction
This document provides step-by-step instructions on how to allow VPN Clients access to the Internet while they are tunneled into a Cisco IOS® Router. This configuration is required to allow the VPN Clients secure access to corporate resources via IPsec and at the same time allow unsecured access to the Internet. This configuration is called split tunneling.
- The Cisco VPN Client is available for both 32bit and 64bit Windows operating systems. To download the latest Cisco VPN Client, simply visit our download section and look for our new Cisco Tools category!
- We would like to inform our readers that we have updated our download section to include Cisco's popular Windows VPN Client. The Cisco VPN Client is available for both 32bit and 64bit Windows operating systems. To download the latest Cisco VPN Client, simply visit our download section and look for our new Cisco Tools category!
Note: Split tunneling can pose a security risk when configured. Since VPN Clients have unsecured access to the Internet, they can be compromised by an attacker. That attacker is then able to access the corporate LAN via the IPsec tunnel. A compromise between full tunneling and split tunneling can be to allow VPN Clients local LAN access only. Refer to PIX/ASA 7.x: Allow Local LAN Access for VPN Clients Configuration Example for more information.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on these software and hardware versions:

Cisco Router 3640 with Cisco IOS Software Release 12.4
Cisco VPN Client 4.8
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to the Cisco Technical Tips Conventions for more information on document conventions.
Background Information
Remote access VPNs address the requirement of the mobile workforce to securely connect to the organization's network. Mobile users are able to set up a secure connection using the VPN Client software installed on their PCs. The VPN Client initiates a connection to a central site device configured to accept these requests. In this example, the central site device is a Cisco IOS Router that uses dynamic crypto maps.
When you enable split tunneling for VPN connections, it requires the configuration of an access control list (ACL) on the router. In this example, the access-list 101 command is associated with the group for split tunneling purposes, and the tunnel is formed to the 10.10.10.x/24 network. Unencrypted traffic flows (for example, the Internet) to devices are excluded from the networks configured in ACL 101.
Apply the ACL on the group properties.
In this configuration example, an IPsec tunnel is configured with these elements:
Crypto maps applied to the outside interfaces on the PIX
Extended authentication (Xauth) of the VPN Clients against a local authentication
Dynamic assignment of a private IP address from a pool to VPN Clients
The nat 0 access-list command functionality, which allows hosts on a LAN to use private IP addresses with a remote user and still get a Network Address Translation (NAT) address from the PIX to visit an untrusted network.
Premier Montauk 3 in. W Firm Angle Sash Paint Brush. 5.0 out of 5 stars 8. Only 10 left in stock - order soon. Premier Riverdale 2 in. W Extra Stiff Angle Sash Paint Brush. Purdy 144152330 XL Series Glide Angular Trim Paint Brush, 3 inch. 4.7 out of 5 stars 2,691. Hand made brushes in the USA, Premier paint brushes will not let you down. Designed for today's paints and stains. Formulated to deliver smooth flow and carry more paint to the end of the brush for fine finishes while achieving it fast. Premier riverdale paint brush.
Configure
Document to pdf converter free online. In this section, you are presented with the information to configure the features described in this document.
Note: Use the Command Lookup Tool (registered customers only) to obtain more information on the commands used in this section.
Network Diagram
This document uses this network setup:
Note: The IP addressing schemes used in this configuration are not legally routable on the Internet. They are RFC 1918 addresses which have been used in a lab environment.
Configurations
This document uses these configurations:
| Router |
|---|
VPN Client 4.8 Configuration
Complete these steps in order to configure the VPN Client 4.8.
Choose Start > Programs > Cisco Systems VPN Client > VPN Client.
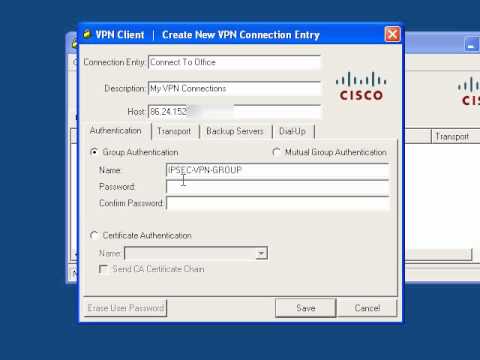
Click New in order to launch the Create New VPN Connection Entry window.
Enter the name of the Connection Entry along with a description, enter the outside IP address of the router in the Host box, and enter the VPN Group name and password. Click Save.
Click on the connection you would like to use and click Connect from the VPN Client main window.
When prompted, enter the Username and Password information for Xauth and click OK in order to connect to the remote network.
The VPN Client gets connected with the router at the central site.
Choose Status > Statistics in order to check the tunnel statistics of the VPN Client.
Go to the Route Details tab in order to see the routes that the VPN Client secures to the router.
In this example, the VPN Client secures access to 10.10.10.0/24 while all other traffic is not encrypted and not sent across the tunnel. The secured network is downloaded from ACL 101 which is configured in the central site router.
Verify
This section provides information you can use to confirm your configuration works properly.
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
show crypto isakmp sa—Shows all current IKE Security Associations (SAs) at a peer.
show crypto ipsec sa—Shows the settings used by current SAs.
Troubleshoot
Troubleshooting Commands
Vpn Client To Site Cisco Router
The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output.
Note: Refer to Important Information on Debug Commands before you use debug commands.
debug crypto ipsec—Displays the IPsec negotiations of Phase 2.
debug crypto isakmp—Displays the ISAKMP negotiations of Phase 1.
Related Information
Objective
In a Client-to-Site Virtual Private Network (VPN) connection, clients from the Internet can connect to the server to access the corporate network or Local Area Network (LAN) behind the server but still maintains the security of the network and its resources. This feature is very useful since it creates a new VPN tunnel that would allow teleworkers and business travelers to access your network by using a VPN client software without compromising privacy and security.
The objective of this document is to show you how to configure Client-to-Site VPN connection on the RV34x Series Router.
Applicable Devices
- RV34x Series
Software Version
- 1.0.01.16
Configure Client-to-Site VPN
Step 1. Log in to the router web-based utility and choose VPN > Client-to-Site.
Step 2. Click the Add button under IPSec Client-to-Site Tunnels section.
Step 3. In the Add a New Tunnel area, click the Cisco VPN Client radio button.
Step 4. Check the Enable check box to enable the configuration.
Step 5. Enter a group name in the field provided. This will serve as identifier for all the member of this group during the Internet Key Exchange (IKE) negotiations.
Note: Enter characters between A to Z or 0 to 9. Spaces and special characters are not allowed for the group name. In this example, TestGroup is used.
Step 6. Click on the drop-down list to choose the Interface. The options are:
- WAN1
- WAN2
- USB1
- USB2
Note: In this example, WAN1 is chosen. This is the default setting.
Step 7. In the IKE Authentication Method area, choose an authentication method to be used in IKE negotiations in IKE-based tunnel. The options are:
- Pre-shared Key — IKE peers authenticate each other by computing and sending a keyed hash of data that includes the Pre-shared Key. If the receiving peer is able to create the same hash independently using its Pre-shared key, it knows that both peers must share the same secret, thus authenticating the other peer. Pre-shared keys do not scale well because each IPSec peer must be configured with the Pre-shared key of every other peer with which it establishes a session.
- Certificate — The digital certificate is a package that contains information such as a certificate identity of the bearer: name or IP address, the serial number expiration date of the certificate, and a copy of the public key of the certificate bearer. The standard digital certificate format is defined in the X.509 specification. X.509 version 3 defines the data structure for certificates.
Note: In this example, Pre-shared Key is chosen. This is the default setting.
Step 8. Enter a pre-shared key in the field provided. This will be the authentication key among your group of IKE peers.
Step 9. (Optional) Check the Enable check box for the Minimum Pre-shared Key Complexity to view the Pre-shared Key Strength Meter and determine the strength of your key. The strength of your key are defined as follows:
- Red— The password is weak.
- Orange— The password is fairly strong.
- Green — The password is strong.
Note: You can check the Enable check box in the Show Pre-shared Key field to check your password in plain text.
Step 10. (Optional) Click on the plus icon in the User Group table to add a group.
Step 11. (Optional) Choose from the drop-down list whether the user group is for admin or for guests. If you created your own user group with user accounts, you can select it. In this example, we will be selecting TestGroup.
Note: TestGroup is a user group that we have created in System Configuration >User Groups.
Note: In this example, TestGroup is chosen. You can also check the box beside the user group and then click the Delete button if you want to delete a user group.
Step 12. Click on a radio button to choose a Mode. The options are:
- Client — This option allows the client to request for an IP address and the server supplies the IP addresses from the configured address range.
- Network Extension Mode (NEM) — This option allows clients to propose their subnet for which VPN services need to be applied on traffic between LAN behind server and subnet proposed by client.
Note: In this example, Client is chosen.
Cisco Vpn Client Windows 10 Download
Step 13. Enter the starting IP address in the Start IP field. This will be the first IP address in the pool that can be assigned to a client.
Note: In this example, 192.168.100.1 is used.
Step 14. Enter the ending IP address in the End IP field. This will be the last IP address in the pool that can be assigned to a client.

Note: In this example, 192.168.100.100 is used.
Step 15. (Optional) Under the Mode Configuration area, enter the IP address of the primary DNS server in the field provided.
Note: In this example, 192.168.1.1 is used.
Step 16. (Optional) Enter the IP address of the secondary DNS server in the field provided.
Note: In this example, 192.168.1.2 is used.
Step 17. (Optional) Enter the IP address of the primary WINS server in the field provided.
Note: In this example, 192.168.1.1 is used.
Step 18. (Optional) Enter the IP address of the secondary WINS server in the field provided.
Note: In this example, 192.168.1.2 is used.
Step 19. (Optional) Enter the default domain to be used in the remote network in the field provided.
Note: In this example, sample.com is used.
Step 20. (Optional) In the Backup Server 1 field, enter the IP address or the domain name of the backup server. This will be where the device can start the VPN connection in case the primary IPSec VPN server fails. You can enter up to three backup servers in the fields provided. The Backup Server 1 has the highest priority among the three servers and the Backup Server 3 has the lowest.
Vpn Client To Site Cisco Password
Note: In this example, Example.com is used for Backup Server 1.
Step 21. (Optional) Check the Split Tunnel check box to enable split tunnel. Split Tunneling allows you to access the resources of a private network and the Internet at the same time.
Step 22. (Optional) Under the Split Tunnel Table, click the plus icon to add an IP address for split tunnel.
Step 23. (Optional) Enter the IP address and netmask of the split tunnel in the fields provided.
Note: In this example, 192.168.1.0 and 255.255.255.0 are used. You can also check the box and click on the Add, Edit, and Delete buttons to add, edit, or delete a split tunnel, respectively.
Step 24. (Optional) Check the Split DNS check box to enable split DNS. Split DNS allows you to create separate DNS servers for internal and external networks to maintain security and privacy of network resources.
Step 25. (Optional) Click the plus icon under the Split DNS Table to add a domain name for split DNS.
Step 26. (Optional) Enter the domain name of the split DNS in the field provided.
Vpn Client To Site Cisco Login
Note: In this example, labsample.com is used. You can also check the box and click on the Add, Edit, and Delete buttons to add, edit, or delete a split DNS, respectively.
Step 27. Click Apply.
Conclusion
You should now have successfully configured Client-to-Site connection on the RV34x Series Router.
Vpn Client To Site Cisco Remote
Click on the following articles to learn more on the following topics:
Vpn Client To Site Cisco Server
View a video related to this article..
