The following sections describe how to install and configure the Apache HTTP Server Plug-In:
- Centos Httpd Proxy Configuration
- Httpd Proxy Configuration List
- Apache Httpd Proxy Server Configuration
Note:
Using Virtualhost and modproxy together. The following example allows a front-end machine to proxy a virtual host through to a server running on another machine. In the example, a virtual host of the same name is configured on a machine at 192.168.111.2. The parent re-reads its configuration files and re-opens its log files. As each child dies off the parent replaces it with a child from the new generation of the configuration, which begins serving new requests immediately. We can run a configuration file syntax test as follows: apachectl configtest apachectl -t. To clarify for future reference, a2enmod, as is suggested in several answers above, is for Debian/Ubuntu. Red Hat does not use this to enable Apache modules - instead it uses LoadModule statements in httpd.conf. Each httpd module manages its own configuration, and each of its directives in httpd.conf specify one piece of configuration in a particular context. Httpd does not execute a command as it is read.
In this release of Oracle WebLogic Server, a single plug-in supports both Apache HTTP Server and Oracle HTTP Server.Install the Apache HTTP Server Plug-In
After you have downloaded the Apache HTTP Server Plug-In, as described in Downloading the Version 1.1 Plug-Ins, you can install it as an Apache module in your Apache HTTP Server installation and link it as a Dynamic Shared Object (DSO).
A DSO is compiled as a library that is dynamically loaded by the server at runtime, and can be installed without recompiling Apache.
Installation Prerequisites
Before you install the Apache HTTP Server plug-in, you must satisfy the following prerequisites:
Download the Apache HTTP Server Plug-In, as described in Downloading the Version 1.1 Plug-Ins.
You have extracted the plug-ins zip distribution to the location of your choice on the target system. For example,
/home/myhome/weblogic-plugins-1.1/.Install JDK 6 if you want to use SSL. The JDK 6 installation is required to use the orapki utility. The orapki utility manages public key infrastructure (PKI) elements, such as wallets and certificate revocation lists, for use with SSL.
You have a supported Apache HTTP Server installation.
The version 1.1 plug-ins are supported on the Apache platforms described in
http://www.oracle.com/technology/software/products/ias/files/fusion_certification.html.A supported version of WebLogic Server is configured and running on a target system. However, it does not need to be running on the system on which you extracted the plug-in zip distribution. See
http://www.oracle.com/technology/software/products/ias/files/fusion_certification.htmlfor the supported WebLogic Server versions.
Installing the Apache HTTP Server Plug-In as a Dynamic Shared Object
The Apache plug-in is distributed as a shared object (.so) for Unix platforms and a DLL for Windows.
To install the Apache HTTP Server Plug-In as a dynamic shared object:
Make sure that the
weblogic-plugins-1.1/libfolder is included inLD_LIBRARY_PATHon Unix systems (and PATH on Windows systems). If you do not do this, you see linkage errors when starting Apache.In the location where you unzipped the downloaded plug-in file, locate
lib/mod_wl.so, orlibmod_wl.dllfor windows . For example,/home/myhome/weblogic-plugins-1.1/lib/mod_wl.so.Verify that the
mod_so.cmodule is enabled.The Apache HTTP Server Plug-In will be installed in your Apache HTTP Server installation as a Dynamic Shared Object (DSO).
DSO support in Apache is based on module
mod_so.c, which must be enabled beforemod_wl.sois loaded.If you installed Apache HTTP Server using the script supplied by Apache,
mod_so.cis already enabled. Verify that mod_so.c is enabled by executing the following command:APACHE_HOMEbinapachectl -l(Where
APACHE_HOMEis the directory containing your Apache HTTP Server installation.)This command lists all enabled modules. If
mod_so.cis not listed, you must rebuild your Apache HTTP Server, making sure that the following options are configured:See Apache 2.2 Shared Object (DSO) Support at
http://httpd.apache.org/docs/2.2/dso.html.Make a copy of the ${
APACHE_HOME}/bin/httpd.conffile for backup.Open the
httpd.conffile.The file is located at
APACHE_HOME/conf/httpd.conf(whereAPACHE_HOMEis the root directory of your Apache HTTP server installation). See a samplehttpd.conffile at Configure the Apache HTTP Server Plug-In.Install the Apache HTTP Server Plug-In module for Apache 2.2.x by adding the following line to your
APACHE_HOME/conf/httpd.conffile. For Windows, specify the .DLL file.Verify the syntax of the
APACHE_HOME/conf/httpd.conffile with the following command:(Where
APACHE_HOMEis the directory containing your Apache HTTP Server installation.)The output of this command reports any errors in your
httpd.conffile or returns:
Configure the Apache HTTP Server Plug-In

After installing the plug-in in the Apache HTTP Server, configure the WebLogic Server Apache Plug-In and configure the server to use the plug-in.
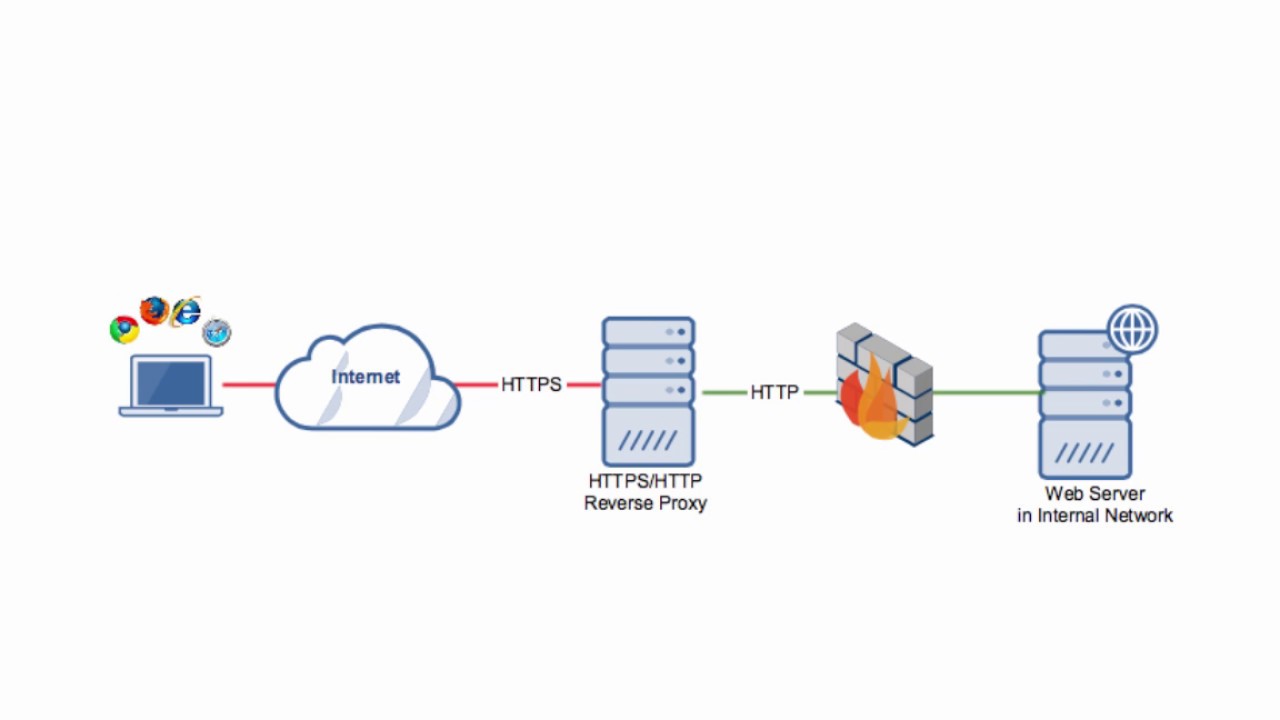
This section explains how to edit the httpd.conf file to proxy requests by path or by MIME type, to enable HTTP tunneling, and to use other WebLogic Server plug-in parameters.
Editing the httpd.conf File
Edit the httpd.conf file in your Apache HTTP server installation to configure the Apache HTTP Server Plug-In.
Make a copy of the ${
APACHE_HOME}/bin/httpd.conffile for backup.Open the
httpd.conffile.The file is located at
APACHE_HOME/conf/httpd.conf(whereAPACHE_HOMEis the root directory of your Apache HTTP server installation). See a samplehttpd.conffile at Configure the Apache HTTP Server Plug-In.Ensure that the WebLogic Server modules are included for Apache 2.2.x. Add the following line to the
httpd.conffile if you have not already done so. For Windows, specify the .DLL file.To proxy requests by MIME type, add an
IfModuleblock that defines one of the following:For a non-clustered WebLogic Server: the
WebLogicHostandWebLogicPortparameters.For a cluster of WebLogic Servers: the
WebLogicClusterparameter.
For example:
To proxy requests by MIME type, add a
MatchExpressionline to theIfModuleblock. Note that if both MIME type and proxying by path are enabled, proxying by path takes precedence over proxying by MIME type.For example, the following
IfModuleblock for a non-clustered WebLogic Server specifies that all files with MIME type .jsp are proxied:You can also use multiple
MatchExpressions, for example:If you are proxying requests by MIME type to a cluster of WebLogic Servers, use the
WebLogicClusterparameter instead of theWebLogicHostandWebLogicPortparameters. For example:To proxy requests by path, use the
Locationblock and theSetHandlerstatement.SetHandlerspecifies the handler for the Apache HTTP Server Plug-In module. For example the followingLocationblock proxies all requests containing /weblogic in the URL:The
PathTrimparameter specifies a string trimmed from the beginning of the URL before the request is passed to the WebLogic Server instance (see General Parameters for Web Server Plug-Ins).Optionally, enable HTTP tunneling for t3 or IIOP.
To enable HTTP tunneling if you are using the t3 protocol and
weblogic.jar, add the followingLocationblock to thehttpd.conffile:To enable HTTP tunneling if you are using the IIOP, the only protocol used by the WebLogic Server thin client,
wlclient.jar, add the followingLocationblock to thehttpd.conffile:
Define any additional parameters for the Apache HTTP Server Plug-In.
The Apache HTTP Server Plug-In recognizes the parameters listed in General Parameters for Web Server Plug-Ins. To modify the behavior of your Apache HTTP Server Plug-In, define these parameters either:
In a
Locationblock, for parameters that apply to proxying by path, orIn an
IfModuleblock, for parameters that apply to proxying by MIME type.
Verify the syntax of the
APACHE_HOME/conf/httpd.conffile with the following command:(Where
APACHE_HOMEis the directory containing your Apache HTTP Server installation.)The output of this command reports any errors in your
httpd.conffile or returns:Start the Apache HTTP Server.
(Where
APACHE_HOMEis the directory containing your Apache HTTP Server installation.)Send a request to
http://apache-host:apache-port/mywebapp/my.jspfrom the browser. Validate the response.
Placing WebLogic Properties Inside Location or VirtualHost Blocks
If you choose to not use the IfModule, you can instead directly place the WebLogic properties inside Location or VirtualHost blocks. Consider the following examples of the Location and VirtualHost blocks:
Including a weblogic.conf File in the httpd.conf File
If you want to keep several separate configuration files, you can define parameters in a separate configuration file called weblogic.conf file, by using the Apache Include directive in an IfModule block in the httpd.conf file:
The syntax of weblogic.conf files is the same as that for the httpd.conf file.
This section describes how to create weblogic.conf files, and includes sample weblogic.conf files.
Creating weblogic.conf Files
Centos Httpd Proxy Configuration
Be aware of the following when constructing a weblogic.conf file.
Enter each parameter on a new line. Do not put '=' between a parameter and its value. For example:
If a request matches both a MIME type specified in a
MatchExpressionin anIfModuleblock and a path specified in aLocationblock, the behavior specified by theLocationblock takes precedence.If you use an Apache HTTP Server
<VirtualHost>block, you must include all configuration parameters (MatchExpression, for example) for the virtual host within the<VirtualHost>block (see Apache Virtual Host documentation athttp://httpd.apache.org/docs/vhosts/).If you want to have only one log file for all the virtual hosts configured in your environment, you can achieve it using global properties. Instead of specifying the same
Debug,WLLogFileandWLTempDirproperties in each virtual host you can specify them just once in the<IfModule>tag.Sample
httpd.conffile:All the requests which match /jurl/* will have Debug Level set to ALL and log messages will be logged to
c:/tmp/global_proxy.logfile. All the requests which match /web/* will have Debug Level set to OFF and no log messages will be logged. All the requests which match /foo/* will have Debug Level set to ERR and log messages will be logged toc:/tmp/foo_proxy.logfile.Oracle recommends that you use the
MatchExpressionstatement instead of the<Files>block.
Sample weblogic.conf Configuration Files
The following examples of weblogic.conf files may be used as templates that you can modify to suit your environment and server. Lines beginning with # are comments.
In Example 3-2, the MatchExpression parameter syntax for expressing the filename pattern, the WebLogic Server host to which HTTP requests should be forwarded, and various other parameters is as follows:
The first MatchExpression parameter below specifies the filename pattern *.jsp, and then names the single WebLogicHost. The paramName=value combinations following the pipe symbol specify the port at which WebLogic Server is listening for connection requests, and also activate the Debug option. The second MatchExpression specifies the filename pattern *.http and identifies the WebLogicCluster hosts and their ports. The paramName=value combination following the pipe symbol specifies the error page for the cluster.
Example 3-2 Example Using Multiple WebLogic Clusters
Example 3-3 shows an example without WebLogic clusters.
Example 3-4 shows an example of configuring multiple name-based virtual hosts.
Example 3-4 Example Configuring Multiple Name-Based Virtual Hosts
You must define a unique value for ServerName or some Plug-In parameters will not work as expected.
Template for the Apache HTTP Server httpd.conf File
This section contains a sample httpd.conf file for Apache 2.2. You can use this sample as a template and modify it to suit your environment and server. Lines beginning with # are comments.
Note that Apache HTTP Server is not case sensitive.
˄˅Open terminal and according to your OS version run the following commands as root to enable Apache HTTP Proxy:
Note •The location of apachectl and htcacheclean will vary based on your system, check it before running the script. •The parameter /var/cache/httpd/proxy determines the location of the caching folder, this location is set in /etc/httpd/conf.d/proxy.conf under CacheRoot. •Apache HTTP Proxy replaces the Mirror Tool functionality from ESET Remote Administrator 6.x. It is primarily used for caching detection engine update files and caching information from ESET LiveGrid®. |
For CentOS 7
1.systemctl enable httpd
2.sudo mkdir -p /etc/systemd/system/httpd.service.requires
3.sudo ln -s /usr/lib/systemd/system/htcacheclean.service /etc/systemd/system/httpd.service.requires
4.systemctl start httpd
5.htcacheclean -d60 -t -i -p/var/cache/httpd/proxy -l10000M

Note You can adjust parameters for Apache HTTP Proxy cache cleaning: -d defines cleaning interval in minutes, -p specifies path as the root directory of the disk cache, -t deletes all empty directories, -i intelligently deletes cache only when there was a modification of the disk cache, -l defines total disk cache size limit. |
6.iptables -A INPUT -p tcp --dport 3128 -j ACCEPT
7.ip6tables -A INPUT -p tcp --dport 3128 -j ACCEPT
Httpd Proxy Configuration List
.svg/1200px-Apache_HTTP_server_logo_(2019-present).svg.png)
8.service iptables save
9.service ip6tables save
Apache Httpd Proxy Server Configuration
This will start Apache HTTP Proxy and enable port 3128 in a firewall. You will need to create policies for all ESET products / ESMC components to communicate via Apache HTTP Proxy and allow the caching of installation files / update files for ESET products. Make sure, the Apache configuration contains the ProxyMatch segment for your server host. For more information see our Knowledgebase article part II. Configure policy settings for client computers.
